My journey into technology started with a beige box and a whole lot of curiosity.
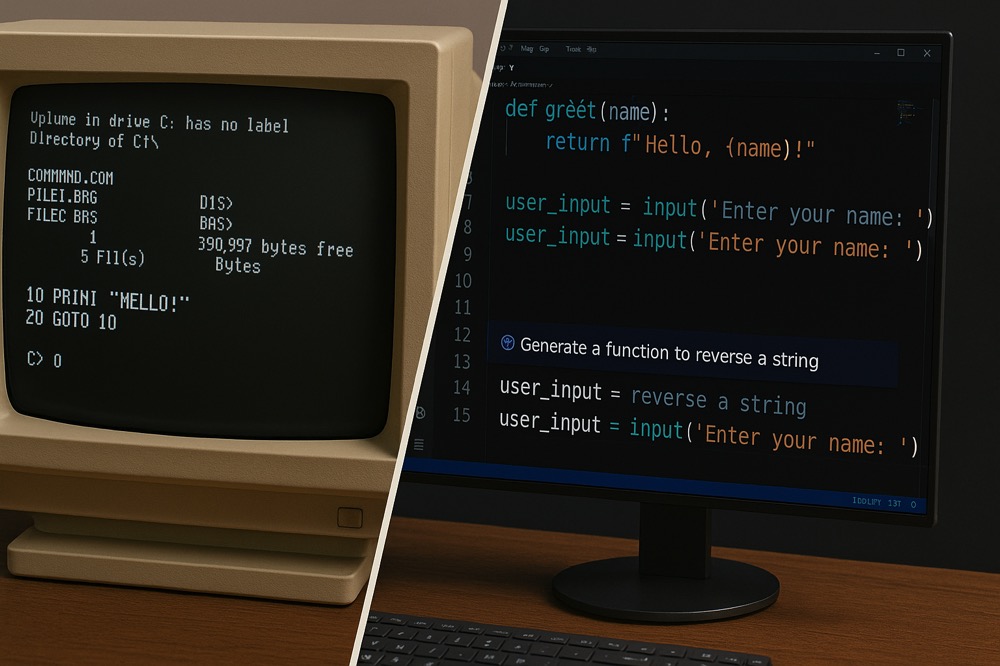
When I was a kid, I got an old 8086 computer. The only thing it came with was a thick manual for 'DOS', its operating system. For a child keen to explore, the blinking C:\> prompt was a mystery. What was I meant to do with it?
I tried typing whatever came to mind, but most of it ended in errors. Then I stumbled upon a command that actually did something interesting: format c:. After I typed 'Y' to confirm, the screen would fill with text, showing me its progress. I didn't realise I was wiping the computer's entire memory. To me, it was just exciting to see it finally spring into action.
The real magic began when I found a book filled with GW-BASIC programs. This changed everything. I wasn't just using a computer anymore; I was telling it what to do. I spent ages carefully typing out code, one line at a time. 10 PRINT "HELLO THERE", 20 GOTO 10. It was slow work, but the feeling of bringing a program to life with my own hands was amazing.
My skills got a boost when QuickBasic started coming with MS-DOS. It felt like a professional setup. The tools were better, the language was more powerful, and I started building my own little games and applications, learning how to organise my ideas into code.
But every programmer eventually hits a wall. For me, it was a 64-kilobyte limit on a single variable. It sounds tiny now, but it was a major roadblock for a project I was passionate about. The only way forward was to learn C, a much more complex language. It was a steep climb, but it was the only way to build bigger and more powerful software.
And that brings me to today.
For most of my career, my job was to translate human ideas into instructions a computer could follow. I had to think like a machine, breaking everything down into small, logical steps.
Now, that's all been turned on its head. I still solve problems, but my process is completely different. I have a conversation with my computer. I can describe a goal, or show it a research paper, and an AI partner helps me write the code. My role has shifted from a builder, laying each brick of code, to an architect, designing the overall structure.
Looking back, the path from blindly typing format c: to working alongside an AI has been incredible. It shows just how far we've come. We've moved from telling the machine exactly how to do something to simply describing what we want to achieve. It's a massive change, and I have a feeling the best is yet to come.