Data-Driven Risk Management
How Peakhour's contextual security aligns with Visa's data-driven risk management approach in the 2025-2028 Security Roadmap.

How Peakhour's contextual security aligns with Visa's data-driven risk management approach in the 2025-2028 Security Roadmap.

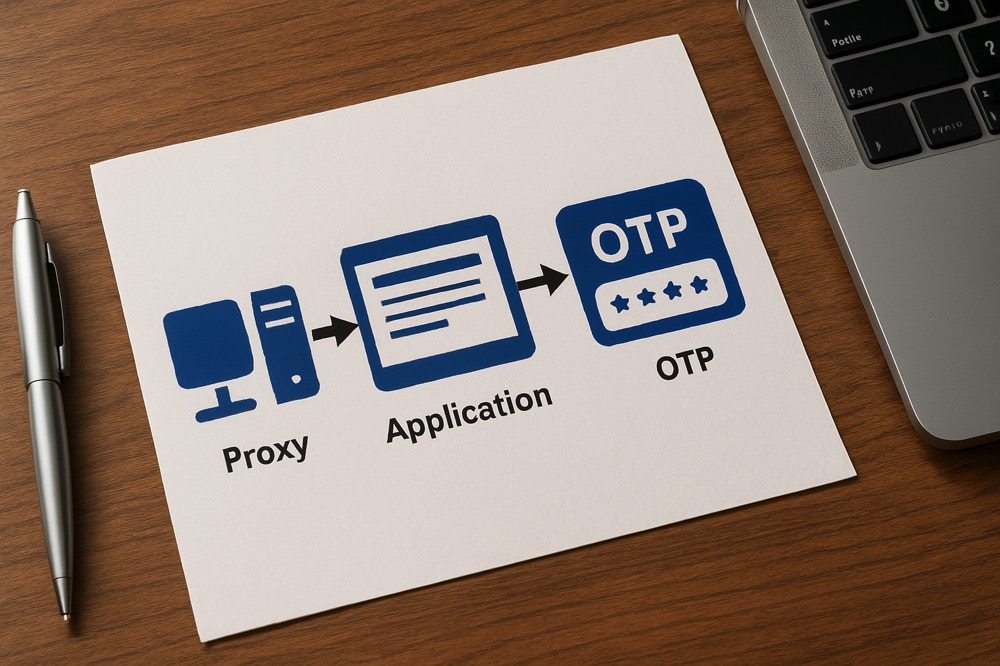
An analysis of how Peakhour's solutions help prevent enumeration attacks, aligning with Visa's Security Roadmap 2025-2028 priorities.

An analysis of Visa's Security Roadmap 2025-2028 and how Peakhour's solutions help Australian businesses meet these security objectives.

Comprehensive analysis of credential stuffing threats against Australian financial institutions and how application security platforms help meet CPS 234 disclosure requirements whilst preventing account takeover attacks.
Comprehensive guide to APRA cybersecurity requirements for Australian financial institutions. Learn how application security platforms help meet CPS 234 compliance and Information Security Manual guidelines for protecting financial services infrastructure.
© PEAKHOUR.IO PTY LTD 2025 ABN 76 619 930 826 All rights reserved.