A Tale Of Two Scoring Systems - The Atlassian Confluence Vulnerabilities

When I first caught wind of the exploits targeting Atlassian Confluence - CVE-2023-22515 and CVE-2023-22518, I knew I had to get on top of it fast. As a widely used commercial application, many of our clients at Peakhour rely on it, and I needed to figure out what to tell them about the threat.
I started by looking into CVE-2023-22515 and CVE-2023-22518. These weren't just minor glitches; they were serious security breaches. Attackers could create unauthorised admin accounts, a real threat to the confidentiality, integrity, and availability of data.
Paul from Secure Stack has already performed an excellent analsysis of the situation and identified the likely scope of the problem. I highly suggest a read for further background and the timelime below is unashamedly lifted from that article.
The Timeline So Far
-
CVE-2023-22515 Impact Analysis: This bug initially hit versions 8.0.x to 8.5.3 of Confluence Server and Data Center products. Luckily, the cloud SaaS versions were spared. Given Confluence's widespread use, especially in large organisations that don't always update their systems, the scope of this was huge.
-
Dealing with CVE-2023-22518: Just a week later, CVE-2023-22518 popped up. It started with a CVSS score of 9.1 and affected every single version of Confluence ever released. This meant even those not hit by the first CVE were now in the firing line.
-
The Severity Upgrade of CVE-2023-22518: Come November 7th, 2023, Atlassian ramped up the severity of CVE-2023-22518 to a CVSS score of 10. The reason? Ransomware exploitation was detected, and like CVE-2023-22515, it allowed creation of admin accounts.
Looking to EPSS for advice
In tackling these CVEs, I leaned heavily on the Exploit Prediction Scoring System (EPSS). EPSS combines info about CVEs with real-world data on actual exploitations. Its goal? To estimate the likelihood of a CVE being exploited in the next 30 days. It dishes out a score between 0 and 1 - the higher the score, the higher the risk. Read more on the applicability on EPSS for scoring vulnerabilities.
EPSS Score Changes I Observed
A major update happened on October 10, 2023, when new threat intelligence came in. This shook up the EPSS score for CVE-2023-22515 big time. I saw a significant jump in the score post-October 10th, indicating a higher threat level due to active exploitation.
As seen in the descending date table:
| Date | EPSS Score | Percentile |
|---|---|---|
| 2023-10-13 | 0.93527 | 0.98809 |
| 2023-10-12 | 0.93527 | 0.98809 |
| 2023-10-11 | 0.93527 | 0.98808 |
| 2023-10-10 | 0.00126 | 0.46728 |
| 2023-10-09 | 0.00126 | 0.46716 |
CVE-2023-2258 is obviously still evoloving with a score change just yesterday:
| Date | EPSS Score | Percentile |
|---|---|---|
| 2023-11-08 | 0.01852 | 0.86954 |
| 2023-11-07 | 0.00061 | 0.24385 |
| 2023-11-06 | 0.00054 | 0.20098 |
| 2023-11-05 | 0.00054 | 0.20099 |
| 2023-11-03 | 0.00054 | 0.20098 |
| 2023-11-02 | 0.00043 | 0.07260 |
| 2023-11-01 | 0.00043 | 0.07283 |
This table reflects a significant increase in the EPSS score from November 1st to November 8th, indicating an escalating likelihood of exploitation.
Making Sense of the EPSS Score Changes
These shifts in EPSS scores tied in with Atlassian's vendor changelog reports:
-
31 Oct 2023: Atlassian's CISO sent out an alert about significant data loss potential. No active exploits were reported yet, but the warning was clear.
-
02 Nov 2023: Critical info about the vulnerability got posted publicly, upping the risk of exploitation.
-
03 Nov 2023: A customer reported an active exploit. It was a wake-up call for anyone who hadn’t patched up.
-
06 Nov 2023: Several active exploits and ransomware uses were observed, leading to the CVSS score escalation for CVE-2023-22518.
I also checked out the CVSS scores. For CVE-2023-22515, it stood at a perfect 10.0. The EPSS score for CVE-2023-22518 also showed notable fluctuations, reflecting an increasing likelihood of exploitation.
EPSS vs. CVSS in My Vulnerability Management Approach
I see EPSS as a gauge of the probability of a vulnerability being exploited, focusing on the threat aspect. It's a piece of the puzzle, not the whole picture. Asset accessibility, vulnerability type, and asset value – these also play crucial roles. I use EPSS alongside CVSS to get a fuller understanding of what we're dealing with. Of interest, we can see how the CVSS scores map to EPSS severity.
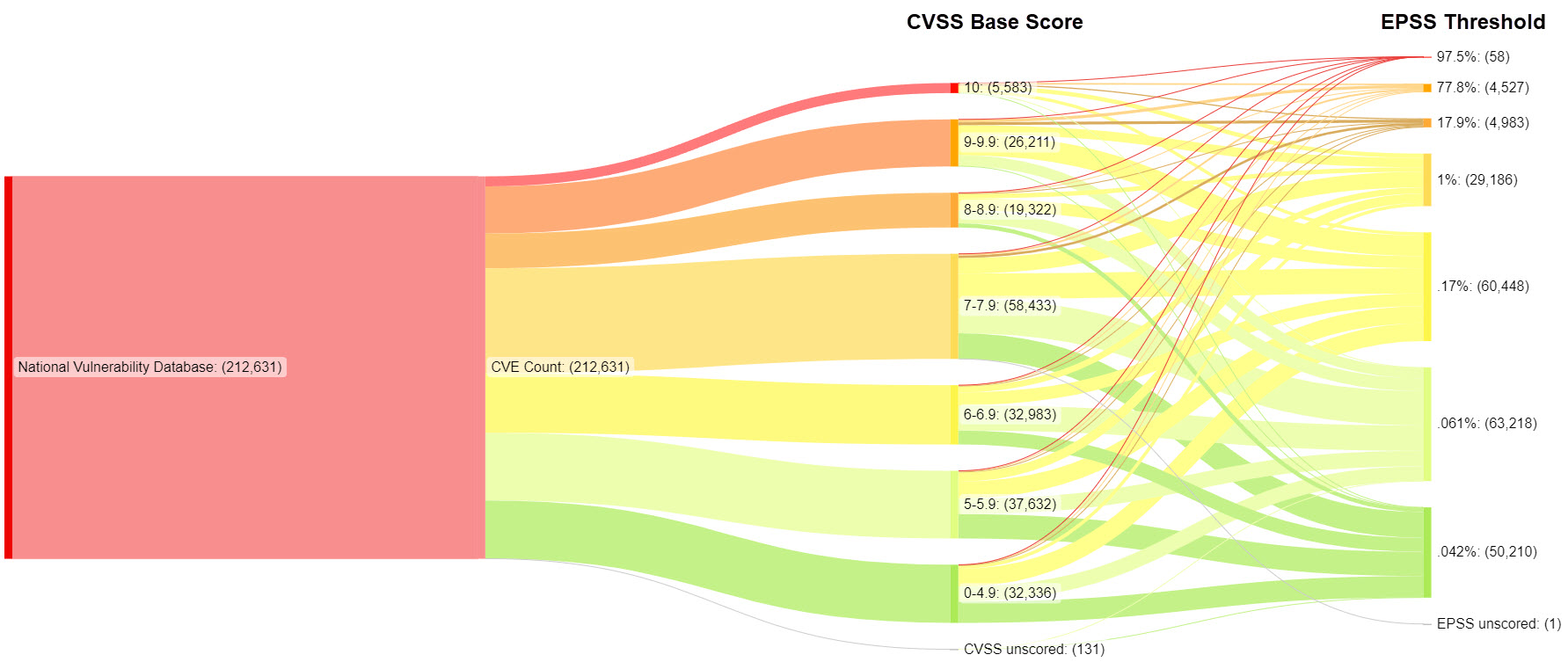
Are Peakhour Clients Protected?
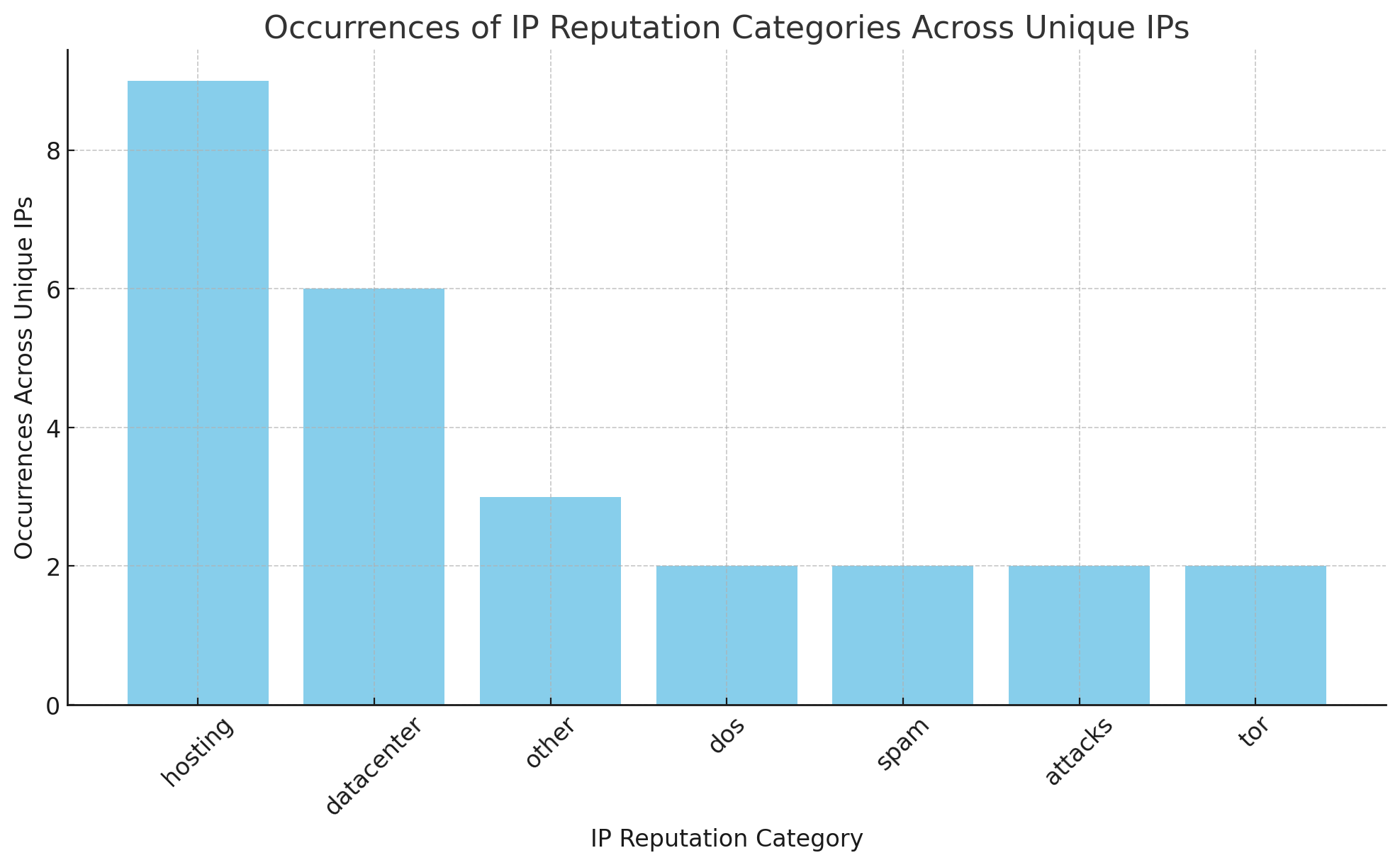
Now we know what we are dealing with, and the real point of this analysis, I turned to Clickhouse to see what was going on. Plugging in the public information about the exploits we quickly observed that we are getting active scans. Our IP Reptuation lists are also actively categorising the IPs - providing clients are suitably using our lists - keeping them under the radar.
This is an active list of IPs we are seeing probing for CVE-2023-2215
| Client IP | IP Reputation Category |
|---|---|
| 178.250.189.169 | hosting |
| 185.220.101.57 | other, dos, spam, attacks, tor, hosting, datacenter |
| 193.187.172.73 | hosting |
| 45.134.26.2 | other |
| 45.94.211.81 | hosting, datacenter |
| 46.231.179.42 | datacenter, hosting |
| 46.38.255.27 | other, dos, spam, attacks, tor, hosting, datacenter |
| 95.111.246.11 | datacenter, hosting |
| 95.85.78.75 | datacenter, hosting |
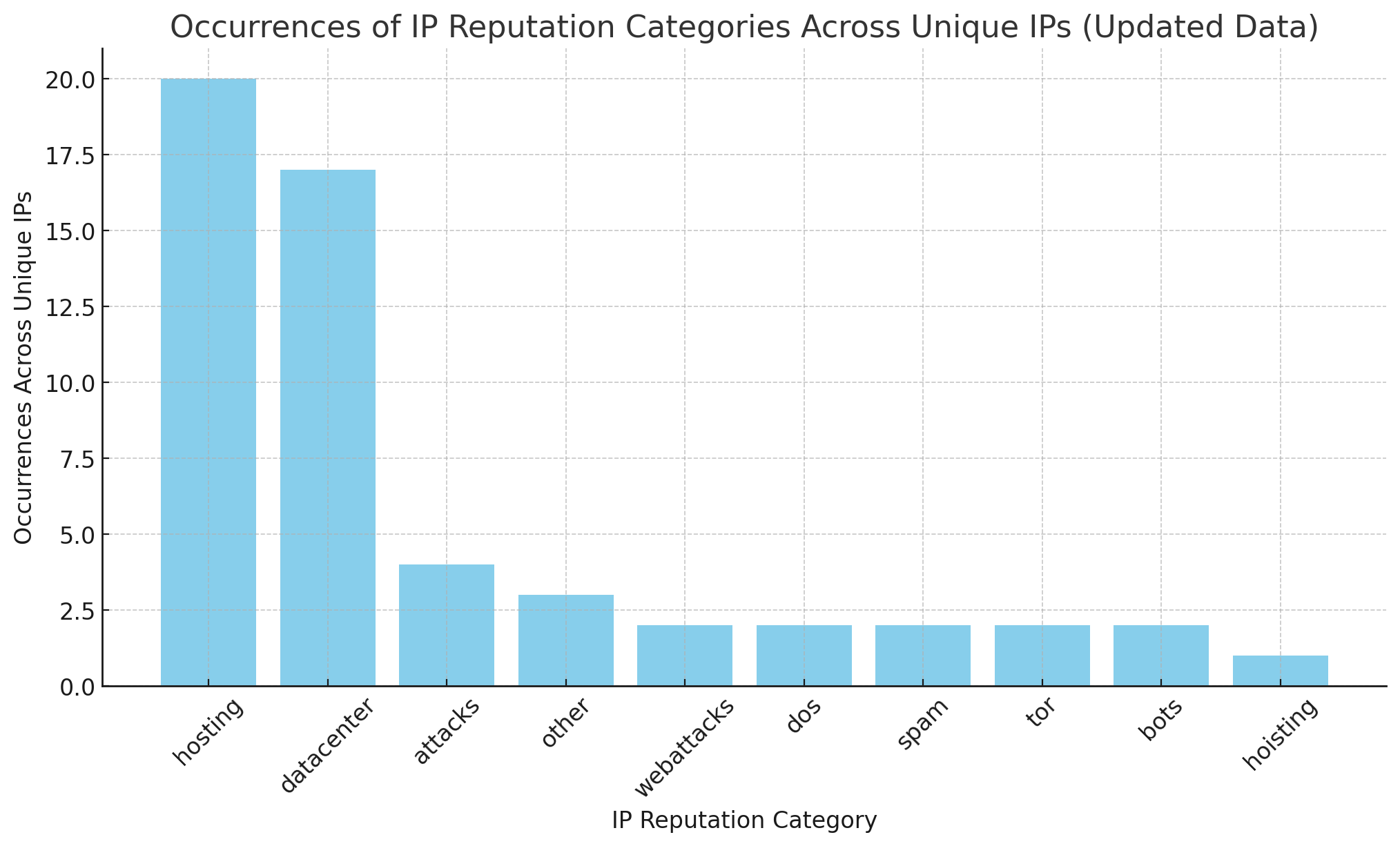
This is a larger list probing for already compromised instances
| Client IP | IP Reputation Categories |
|---|---|
| 104.234.140.11 | webattacks, hosting, datacenter |
| 104.234.140.21 | hosting, datacenter |
| 104.234.140.4 | hosting, datacenter |
| 104.234.140.8 | webattacks, hosting, datacenter |
| 144.172.76.65 | hosting, datacenter, attacks |
| 162.240.159.247 | hosting, datacenter |
| 172.233.176.52 | hosting, datacenter |
| 178.250.189.169 | hosting |
| 185.220.101.57 | other, dos, spam, attacks, tor, hosting, datacenter |
| 193.187.172.73 | hosting |
| 193.29.56.19 | hosting |
| 20.68.177.203 | hosting, datacenter |
| 203.145.142.86 | attacks, bots |
| 37.221.173.253 | hosting, datacenter |
| 45.134.26.2 | other |
| 45.248.160.61 | bots |
| 45.94.211.81 | hoisting, datacenter |
| 46.231.179.42 | datacenter, hosting |
| 46.38.255.27 | other, dos, spam, attacks, tor, hosting, datacenter |
| 54.161.151.64 | hosting, datacenter |
| 92.119.179.90 | datacenter |
| 95.111.246.11 | datacenter, hosting |
| 95.85.78.75 | datacenter, hosting |
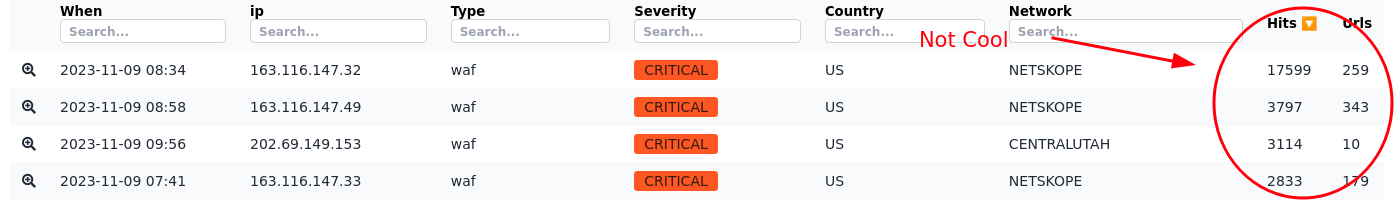
The immediate value of utilising comprehensive, real-time threat intelligence into your active security measures pays off. This not only keeps you 'under the radar', but gives proactive intelligence as to the potential actors probing your applications.
Lastly, we see evidence of follow up attacks post-scan.
What other protections could be applied
Other critical measures like bot mitigation and web application firewalls (WAFs) play a pivotal role in cybersecurity. Bot mitigation strategies are crucial in actively blocking automation attempts that often lead to security breaches. These tools are designed to differentiate between legitimate human traffic and automated bots, effectively thwarting various types of automated attacks such as credential stuffing, scraping, and DDoS attacks. By implementing bot mitigation, organisations can prevent malicious bots from exploiting vulnerabilities, even those yet to be patched or identified in the vulnerability backlog.
Web Application Firewalls, on the other hand, provide a robust line of defense for web applications. They monitor, filter, and block potentially harmful traffic and requests to and from a web application. By using a set of predefined or customisable rules, WAFs can prevent many common web-based attacks such as SQL injection, cross-site scripting (XSS), and others that might exploit known vulnerabilities. The dynamic nature of WAFs allows for a quick response to emerging threats, offering an additional layer of security that adapts to the evolving landscape of cyber threats. Together, bot mitigation and WAFs form a comprehensive defense mechanism that enhances an organisation's ability to protect against a wide array of cyber threats.
Addressing the Backlog of Security Vulnerabilities and Patch Timelines
The Challenge of a Growing Vulnerability Backlog
A significant challenge faced by many security teams is the ever-growing backlog of security vulnerabilities. The data reveals a concerning scenario: 47% of security leaders report having a backlog of applications identified as vulnerable. Even more alarming, 66% state their backlog includes over 100,000 vulnerabilities. This accumulation represents a considerable risk, as vulnerabilities are potential entry points for cyberattacks.
Patching Pace vs. Vulnerability Escalation
Comparing this with the escalation timeline of CVEs from the EPSS and CVSS data provides a stark contrast. Let's consider CVE-2023-22515 and CVE-2023-22518 as examples:
-
CVE-2023-22515 and CVE-2023-22518 Escalation: These vulnerabilities quickly escalated in severity and exploitability. For instance, CVE-2023-22518's CVSS score escalated to 10, and its EPSS probability score indicated a high likelihood of exploitation shortly after discovery.
-
Patch Timelines: The data indicates that 78% of respondents take longer than 3 weeks to patch high-risk vulnerabilities, with 29% needing more than 5 weeks. This delay in patching is critical given the rapid escalation and exploitation of vulnerabilities like CVE-2023-22515 and CVE-2023-22518.
The Gap Between Detection and Remediation
This disparity between the quick escalation of vulnerabilities and the slower patching process is a significant gap in cybersecurity defenses. The rapid increase in EPSS scores for vulnerabilities like CVE-2023-22518 signifies an immediate threat, yet many organisations struggle with a lengthy patching process. During this time, the risk of exploitation remains high, leaving systems vulnerable to attacks.
If I could take one scoring system to an island, which would I take?

Both the Exploit Prediction Scoring System (EPSS) and the Common Vulnerability Scoring System (CVSS) offer valuable insights, but for different reasons. My preference leans towards EPSS, primarily due to its straightforward presentation of the likelihood of exploitation. EPSS provides a clear-cut percentage indicating the probability of a vulnerability being exploited, which is not only intuitive but also highly effective in assessing immediate threats.
This direct and quantifiable approach of EPSS makes it particularly useful in conveying the urgency and risk associated with a vulnerability to both technical and non-technical staff. It simplifies the communication process, allowing for a more accessible understanding of the threats, especially for those who may not be deeply versed in cybersecurity jargon. The ability to translate complex security risks into a simple probability score is invaluable in making informed and timely decisions about prioritising and addressing vulnerabilities.
While CVSS is undoubtedly useful in indicating how critical a vulnerability is, its complexity and the multifaceted nature of its scoring system can sometimes be less straightforward to interpret. CVSS scores focus on the severity of the vulnerability itself, considering factors like impact and exploitability. However, they don’t always directly correlate to the immediate threat level in the same clear manner as EPSS scores.
What next from here?
Going through EPSS and CVSS scoring systems in light of the Confluence-Ageddon provides value to security professionals reviewing their on-going risks. If you are in need of immediate defence, reach out, we'd be glad to help. You could protect your self-hosted Confluence with a simple DNS change.
