Recent customer account takeovers have highlighted the growing need for robust security measures. Our 2024 survey of Australian CISOs and CTOs provides insights into how businesses are adapting their web application security and account protection strategies to meet these challenges, particularly in response to credential stuffing attacks and the emerging threat of residential proxies.
Account Protection: Current State and Future Plans
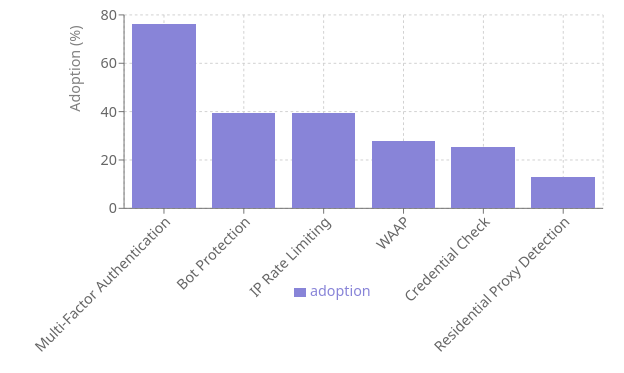
Our survey found 76.23% of Australian businesses use Multi-Factor Authentication (MFA). While this indicates a recognition of security needs, it also reveals gaps in comprehensive protection strategies.
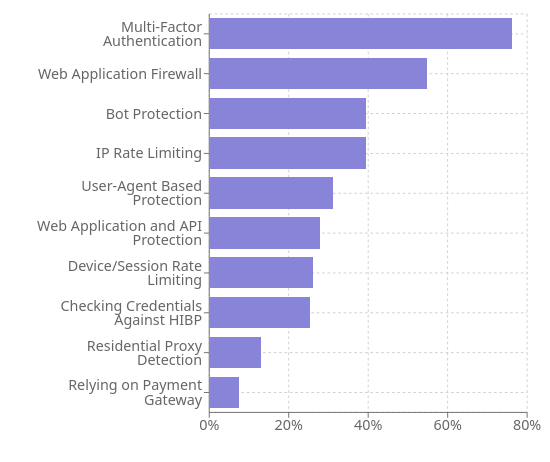
Notably, 39.34% of organisations currently implement bot protection, a crucial defence against automated attacks like credential stuffing. This figure, while concerning, is set to improve, with 34.65% of businesses planning to implement bot protection in the future.
These statistics demonstrate a growing awareness of the need for more comprehensive security measures beyond MFA alone.
Current Bot Management Solutions
Our survey revealed interesting insights into the bot management solutions currently employed by Australian businesses. Cloudflare emerged as the clear leader, with nearly half of the respondents using their services.
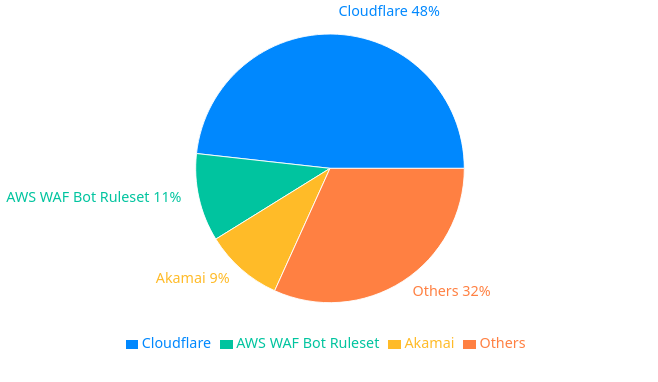
The breakdown of bot management solutions is as follows:
- Cloudflare: 48.24%
- AWS WAF Bot Ruleset: 10.59%
- Other solutions make up the remaining percentage
This distribution highlights a significant market concentration, with Cloudflare dominating the landscape. However, it also reveals opportunities for other providers to increase their market share, particularly in addressing emerging threats like those posed by residential proxies.
The choice of bot management solution can significantly impact a business's ability to detect and mitigate sophisticated attacks, including those leveraging residential proxies. As the threat landscape evolves, we may see shifts in this distribution as businesses seek more advanced protection measures.
The Rising Threat of Residential Proxies
A key finding from our survey is the low adoption rate of residential proxy (resip) detection, with only 13.11% of organisations currently using this technology. However, businesses are recognising the growing threat posed by resips, with a significant number planning to implement resip detection in the near future.
Resips pose a unique challenge to account security by making malicious traffic appear legitimate. They enable attackers to:
- Bypass traditional IP-based rate limiting
- Evade geolocation-based restrictions
- Conduct large-scale credential stuffing attacks
- Scrape sensitive data undetected
The planned adoption of resip detection technology indicates a shift in security strategies to address this emerging threat.
Learn more about the threat of residential proxies and how to detect them
Credential Stuffing: A Persistent and Growing Concern
Credential stuffing attacks continue to be a major concern for businesses. These attacks exploit the common practice of password reuse across multiple sites, allowing attackers to gain unauthorised access to user accounts.
The survey reveals a growing recognition of this threat, with businesses planning to implement various measures to combat credential stuffing:
- 34.65% plan to implement bot protection
- 32.67% intend to add multi-factor authentication
- 31.68% aim to check credentials against known breaches
These planned implementations demonstrate the industry's move towards more robust, multi-layered security approaches.
Mobile Applications: An Emerging Attack Surface
While mobile applications weren't directly addressed in our survey, the data suggests a potential oversight in mobile security strategies. The low adoption rate of Web Application and API Protection (WAAP) - implemented by only 27.87% of respondents - indicates many businesses may be underprepared to protect their mobile assets.
As mobile apps increasingly become primary interfaces for critical operations, this gap in protection leaves businesses vulnerable to attacks, including those leveraging resips.
Balancing Security and User Experience
As businesses recognise the need for enhanced security measures, they also face the challenge of maintaining a positive user experience. Key considerations for enhancing account protection while preserving usability include:
- Expanding beyond MFA
- Implementing bot protection
- Adopting WAAP solutions
- Monitoring credential leaks
- Focusing on API security
- Implementing residential proxy detection
Explore strategies for balancing security and user experience
Executive vs Engineer Perspectives
Our survey revealed differences in cybersecurity priorities between executives and engineers:

Figure 3: Comparison of cybersecurity priorities between executives and engineers
These differences highlight the need for a comprehensive approach to cybersecurity that addresses concerns at all levels of an organisation, including the emerging threat of RESIPs.
Final Thoughts
Our 2024 survey results demonstrate a growing recognition among Australian businesses of the need for enhanced account protection measures. While gaps in security strategies persist, particularly regarding resip detection and mobile application security, the planned implementation of various security measures indicates a positive trend towards more comprehensive protection.
As the threat landscape evolves, with resips emerging as a significant concern, businesses must continue to adapt their security strategies. By implementing multi-layered security solutions that address the full spectrum of threats, from credential stuffing to resip-based attacks, Australian businesses can better protect their assets, reputation, and customer trust in an increasingly complex digital environment.