IP Threat Intelligence
Threat intelligence enables organisations to make proactive decisions in the fight against cyber attacks. One of the most common forms of threat intelligence in cyber security is in the form of IP reputation lists. For example, a given IP address might have a poor reputation for spamming, ddos attacks, malware, and several other categories. IP reputation lists often form a front line of defense in Web Application Firewalls and cyber security solutions.
How Peakhour uses IP threat intelligence
Peakhour boasts extensive threat intelligence capabilities, supporting over 20 categories including:
Active DDoS attacks
Brute forcing
Active attackers
Computers infected with malware
Anonymous Proxies
Forum Spammers
TOR anonymous users
IPs with poor reputation
Unroutable and unassigned IPs
Robots and web scrapers
Datacenter
Hosting Provicers
Crawlers
And More
Customers have access to all 10 lists which can be enabled as straight blocklists, or used as a part of a custom firewall rule, rate limiting rule, or page rule. For example you may want to disallow POSTs from Forum spammers, rate limit Proxies, and outright deny traffic from known Bruteforcing IPs.
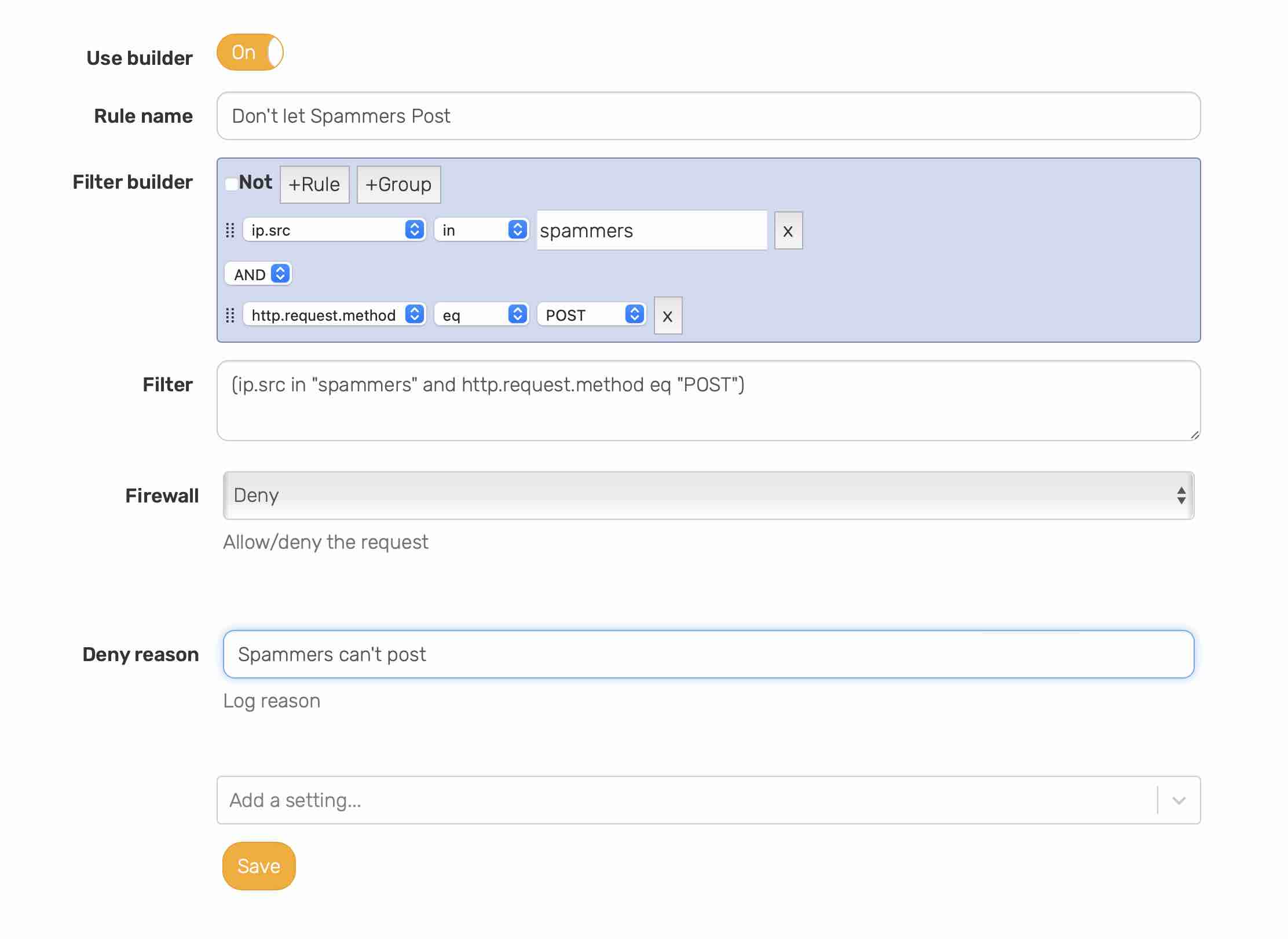 Creating a spammer can't post rule
Creating a spammer can't post rule
How does Peakhour assemble these lists?
The IP reputation lists are sourced from various third party sources, including open source intelligence feeds (OSINT), commercial feeds, community feeds, and our own threat intelligence. IPs are categorised into our pre-defined lists and made available for consumption by the WAF and rules engine. Each list is re-evaluated and constantly updated based on the update schedule of the data provider, some are updated each minute!
Internally managed feeds include verified bot sources that are verified using reverse DNS lookups, PTR record lookups, and WHOIS verification (such as Facebook IPs). WAF hits amongst several customers are consolidated and made available as the Active Attacker list, which is updated in near real time. Our Malware and C&C nodes lists are generated from various partnerships.
The Anonymous Proxies list are known open proxies, services that relay traffic without authentication, whilst our targeted VPN list tracks known third party VPN services.
IPs are fed back into our system for re-evaluation to help source new emerging behaviour within our customer data.
Data visualisation
Any request coming from an IP that matches a blocklist gets tagged with which lists it belongs to. Firewall events are enriched with this information allowing visibility into security threats. This information can assist you with how to handle requests, whether they should be blocked, rate limited or observed.
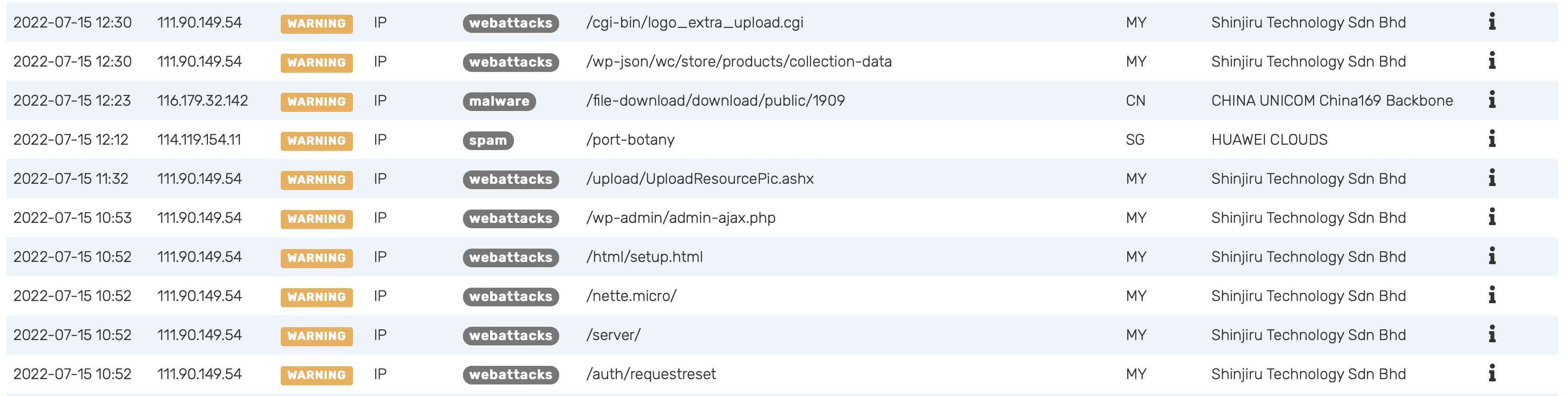 Firewall events generated by reputation matches
Firewall events generated by reputation matches
Blocks generated by our reputation lists can also be viewed in our analytics section.
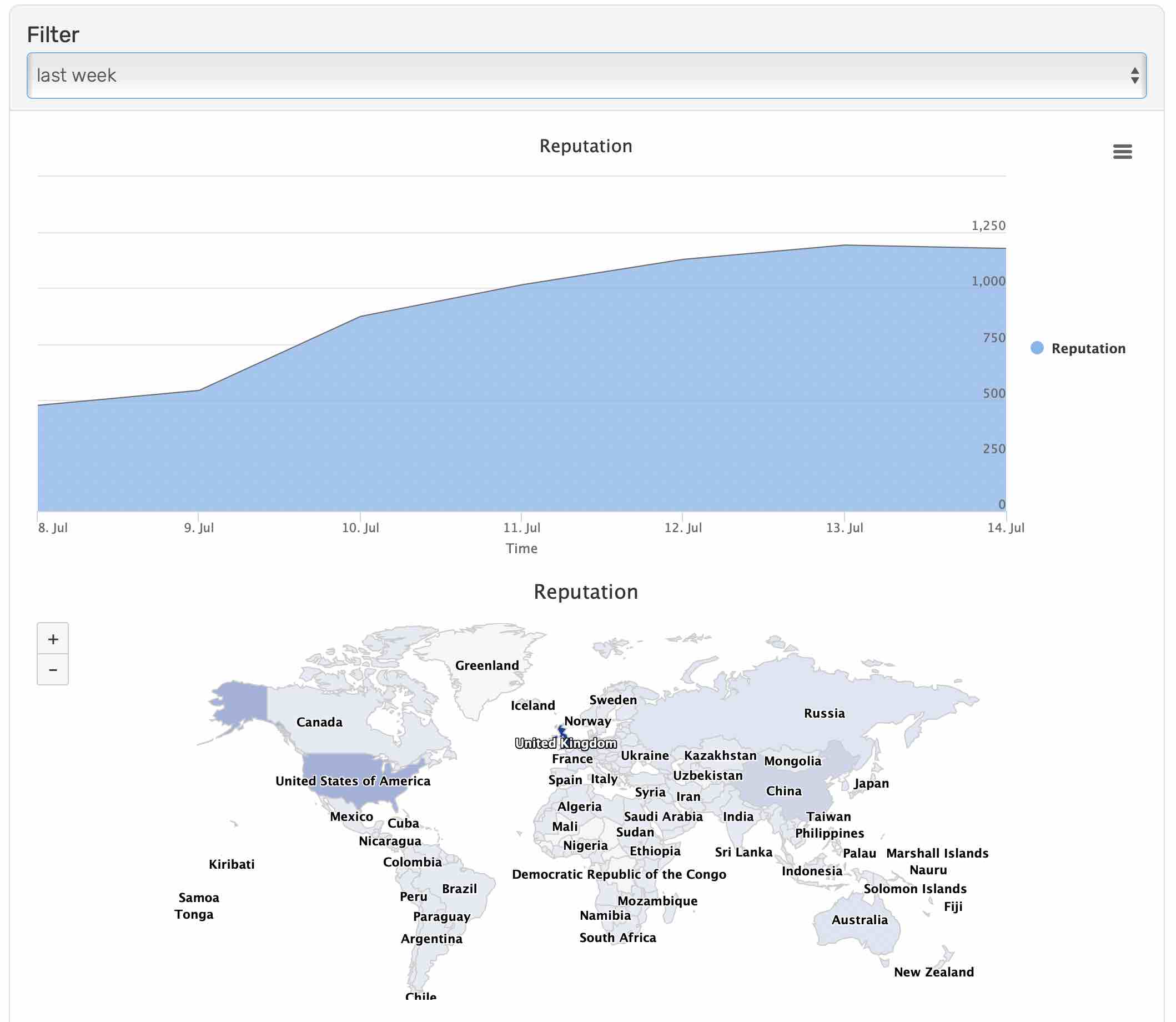 Firewall events generated by reputation matches
Firewall events generated by reputation matches
Future work
We are working on sourcing and collecting additional data to further refine and expand our lists. This includes further segregating our data centre lists and categorising IPs that find their way onto several lists. We are also introducing our threat research centre, to discover possible threat and enrich data blocked by our WAF only.
Conclusion
IP threat intelligence adds a critical layer of security to any cyber defense system. Knowing Peakhour sources and maintains up to date, quality threat intelligence, enables our clients to better protect themselves and stay ahead in the fight against would be attackers.

