Rate limits protect web applications from clients performing excessive requests. Peakhour.IO fully supports rate limits with sophisticated methods for selecting clients to rate limit and the types of rate limits that may be employed.
What kinds of attacks are stopped by rate limiting
When protecting an application using rate limiting, several types of attacks are considered:
- Brute force and enumeration attacks
- Denial of Service (DoS) and Distributed Denial of Service (DDoS)
- Site scraping
- Vulnerability Scanners
What else can rate limiting protect
Public APIs and authenticated APIs can be subject to both abuse or miss use. Sensible rate limit policies can be applied on these endpoints to prevent both attack and maintain service availability. Rate limiting can protect:
- APIs
- Overzealous 'good bots'
How does it work?
Rate limiting focuses on a connecting client and their IP address. The following measures are available for tracking client requests for rate limiting:
- Concurrent connections
- Connections per interval
- Hits per interval
- HTTP 4xx responses per interval
- HTTP 5xx responses per interval
- Custom criteria
How granular can rate limiting be?
Through the use of wirefilter rules, rate limiting can identify clients using both the HTTP request and response and allows segregation of rate limits. For example the URL /api can be rate limited separately to the /login endpoint. Rate limits can be set on response codes, for example the endpoint /search can be protected from scraping by rate limiting clients with excessive 4xx response codes.
What types of criteria can be used to define rate limits?
Rate limits can include any information defined in a HTTP request and response, including:
- IP address
- URL
- Query string
- Headers
- Response codes
- GeoIP information such as ASN or country code
- Parsed user agent information allowing differing rules for search engines vs generic 'bots'
- Various meta information we make available from our BOT protection service
Defining your rate limits
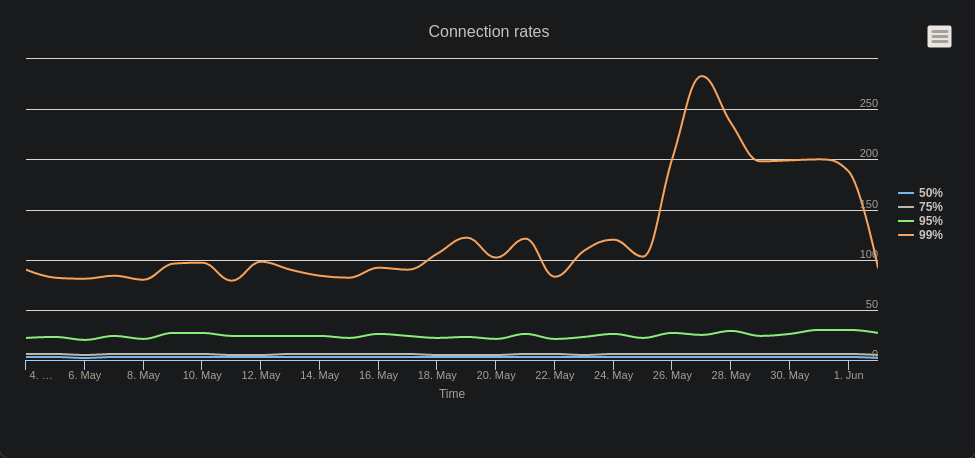
Picking sensible rate limits can be difficult without adequate analytics as to how the web application is typically used. The Peakhour dashboard includes rate based analytics to help with set up.
Learn how Peakhour's Application Security Platform combines high-performance CDN capabilities with comprehensive security controls. Our integrated approach delivers superior caching performance whilst maintaining advanced threat protection for your applications and APIs. Contact our team to discover how advanced rate limiting can improve application performance and security posture.