
Agentic AI vs. Your API
Understand the shift from scripted bots to reasoning AI agents and how to adapt your security strategy for this new reality.

Understand the shift from scripted bots to reasoning AI agents and how to adapt your security strategy for this new reality.

Analysis of attempts to exploit a recent Share Point zero day vulnerability reveal network fingerprinting and classification is a robust defense.

We've gone from command lines to graphical interfaces. The next great leap in how we interact with computers won't be seen, it will be understood. AI is poised to become the ultimate translator between human intent and machine execution.

Exploring how AI can dramatically accelerate the process of turning complex academic research into functional code, with examples from anomaly detection to small LLMs.
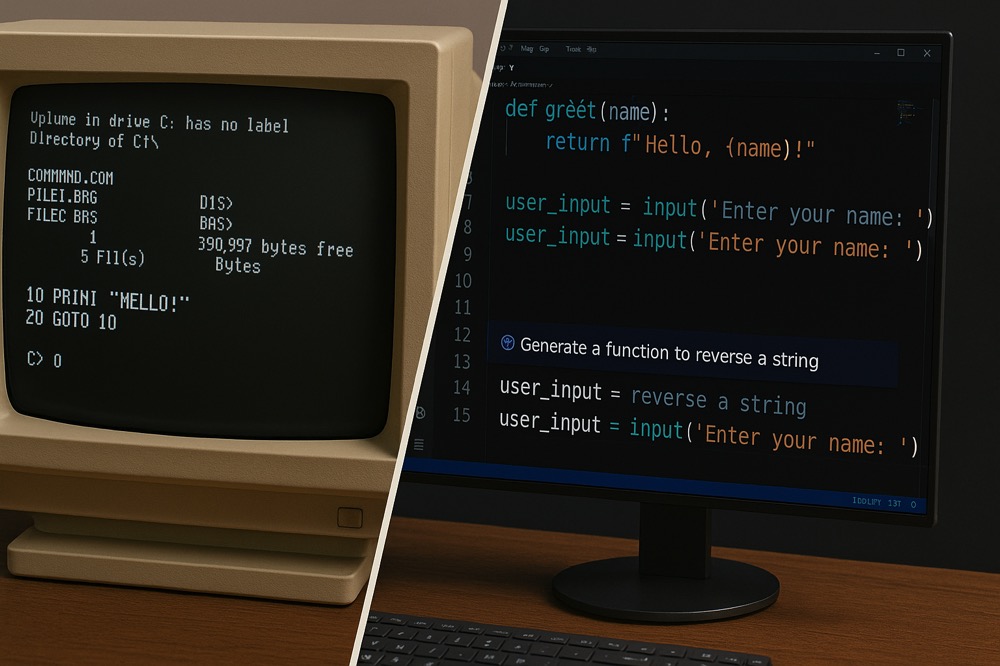
A personal journey through the evolution of programming, from the early days of DOS and BASIC to the current age of AI-assisted coding.

AI agents with reasoning capabilities like DeepSeek are revolutionizing exploit development, marking the end of traditional security approaches based on static rules and patterns.

How open reasoning models transform automation from rigid scripts to autonomous agents, fundamentally changing our approach to security and digital interactions.

Anti-detect browsers represent one of the most sophisticated threats facing modern web applications and APIs. Learn how these tools work, why they pose a significant threat to application security, and how modern security platforms can detect and mitigate their use.

Comprehensive analysis of AI-powered cyber threats and how modern application security platforms defend against machine learning-driven attacks. Learn advanced defence strategies for the AI cybersecurity arms race.

Comprehensive guide to enterprise bot management for modern application security platforms. Learn how to protect applications and APIs from sophisticated bot threats including anti-detect browsers, credential stuffing, and automated attacks targeting DevOps environments.

Comprehensive analysis of credential stuffing threats against Australian financial institutions and how application security platforms help meet CPS 234 disclosure requirements whilst preventing account takeover attacks.

Our 2024 survey reveals Australian businesses are increasingly recognising and addressing account protection challenges, with a focus on combating credential stuffing attacks and the emerging threat of residential proxies.

An analysis of Peakhour's role in addressing key cloud security categories identified in recent industry analysis, demonstrating its comprehensive approach to modern cloud security challenges.

Comprehensive guide to breached credentials protection within modern application security platforms. Learn how to defend against credential stuffing attacks using advanced risk profiling and contextual security measures.
Understand CVSS by examining the Atlassian CVE-2023-22515 and CVE-2023-22518.

An in-depth exploration of EPSS, its data-driven approach to assessing cybersecurity threats, and how it complements CVSS.

Reviewing the CVSS an EPSS CVE scoring systems in light of the Atlassian Confluence-Aggedon

ModSecurity's end-of-life marks a pivotal moment in application security evolution. Discover how modern Application Security Platforms are advancing beyond traditional WAF approaches to provide comprehensive protection for web applications and APIs at the edge.

A comprehensive look at OpenBullet, its capabilities, and the implications for cybersecurity in the face of its misuse.

Explore residential proxies within the context of the MITRE ATT&CK framework, highlighting the security implications and ethical considerations.

Deep dive into Robust Random Cut Forest (RRCF) implementation for real-time anomaly detection in Application Security Platforms. Learn how advanced machine learning algorithms enhance threat detection and automated response capabilities.

Comprehensive guide to application performance optimisation with integrated security testing. Learn how modern Application Security Platforms deliver superior performance whilst maintaining robust threat protection for contemporary applications.
© PEAKHOUR.IO PTY LTD 2025 ABN 76 619 930 826 All rights reserved.